SECURE YOUR WORLD
In today’s digital environment, cyber threats are more sophisticated and pervasive than ever before. Organizations of all sizes and industries are facing unprecedented challenges in safeguarding their data, systems, and operations.
To stay protected from cyber threats, it’s essential to understand the importance of cybersecurity, be aware of the threats out there, and what actions you can take to stay secure.
Organizations who suffered a cyberattack had adverse costs of $250,000 or more.
The percentage of companies who reported having at least one cyberattack in 2023.
The global average cost of a data breach in 2024 — a 10% increase over last year and the highest total ever.
Tracking the Surge in Cyberattacks
Cyberattacks are on the rise, posing significant risks to organizations no matter their size. These threats are growing in number and sophistication due to the nefarious use of artificial intelligence, social engineering tactics, and ransomware.
Check out these recent cyberattacks that impacted organizations across the globe.
Annual Safeguards
Regular checkups of your organization’s cybersecurity systems are essential for maintaining strong protection. If you’re not evaluating key areas on an annual basis, you may be leaving gaps in your defenses that could expose your organization to potential attacks.
Conduct Penetration Testing
Penetration tests are a valuable tool for evaluating the effectiveness of your cybersecurity. These simulated attacks — performed by a cybersecurity expert — probe your defenses to identify weaknesses before real threats can exploit them. With any potential vulnerabilities identified, you’ll learn where improvements can be made to protect against future attacks.
Benefits
- Identifies vulnerabilities
- Safeguards your sensitive data
- Improves your cybersecurity efforts
- Reduces risk of future cyberattacks
- Provides a third-party opinion on your cybersecurity
Review Cyber Insurance Policies
It’s always wise to have a plan in place to mitigate financial losses in case a cyberattack succeeds. One option is a cyber insurance policy, which can help cover the costs of financial losses resulting from a cyberattack or data breach. While not considered a facet of your cybersecurity defenses, it can be a great resource to have in case the unthinkable happens.
Benefits
- Gives you peace of mind
- Assists with legal support
- Provides financial protection
- Helps your operations resume after an attack
Every organization carries the risk of a cyberattack. Because of this, taking proactive measures is critical for incident recovery as well as continued operations. Before purchasing or renewing cyber insurance coverage, review these four factors to ensure you purchase the correct coverage for you and your organization.
Implement Cybersecurity Training Programs
Even with a state-of-the-art cybersecurity system, a single click on a malicious email link can compromise your defenses. That’s why it’s critical to continuously train your employees on cybersecurity best practices.
Benefits
- Minimizes the risk of breaches due to human error
- Mitigates liability as employees verify they’ve completed training
- Trains employees on how to spot the most common cyberattacks, such as phishing emails
- Boosts employee confidence, knowing they play a significant role in protecting the organization
Like any other type of education, repetition is the best way to solidify the knowledge and keep it top of mind for your employees. Having monthly or quarterly cybersecurity training sessions is an effective part of your overall cybersecurity strategy.
Evaluate and Modify Incident Response Plans
It’s crucial to have an incident response plan ready before it’s needed. To ensure you’re prepared for any potential cyberattack, it’s important to regularly review and update your incident response plan. This way you’ll be ready to respond effectively, even if a cyber attack disrupts your access to the plan.
Benefits
- Prepares your organization for unforeseen events
- Familiarizes your staff with the plan on an annual basis
- Adapts your response plan and accounts for emerging threats
- Quickly gets your operations up and running after a cyberattack
Backup Data and Review Data Retention Policies
A key piece of a structured cybersecurity plan that often gets overlooked is regularly backing up your data and ensuring your data retention procedures follow your retention policies.
Benefits
- Safeguards critical organization data in the event it’s initially lost
- Familiarizes your team with your data retention procedures and policies
Routinely and frequently backing up data and reviewing and updating your data retention policies will minimize the impact of any attack.
Review and Update Business Continuity & Disaster Recovery Plan
If essential parts of your operations suddenly stopped working, would you know how to keep things running even if you’re not fully operational? If your answer is no, it's important to create a business continuity and disaster recovery plan right away. If you already have one, make sure to review and update it every year.
Benefits
- Enables your team to anticipate threats and know the response plan
- Modifies your recovery plans to account for new operations and functions
- Reduces the negative impact done to your organization if critical operations are lost
The best time to have a plan is before you actually need it. To support both your clients and employees, it's essential to keep an updated recovery plan in place. This ensures that your organization can continue running smoothly, even if you temporarily lose access to critical functions while resolving the issue.
Safeguards for Individuals
Cybersecurity is vital for individuals to safeguard personal information, financial assets, and privacy. In today’s digital age, numerous threats can compromise sensitive information and cause significant financial and reputational damage. By understanding the importance of cybersecurity and implementing best practices, individuals can mitigate risks and ensure a safer digital environment.
Routinely Change and Use long, Varied Passwords
Hackers may try to access your accounts multiple times over a period of time. Regularly changing your passwords lowers the risk of repeated access. Passwords that combine upper and lowercase letters, numbers, and symbols are much harder for hackers to break, making your accounts more secure.
Set Up Multifactor Authentication On Your Accounts
Multifactor authentication (MFA) provides an extra layer of security, making it much harder for cybercriminals to gain access. This added protection significantly reduces the chances of successful phishing and malware attacks.
Shut Down Your Laptop While in Transit
For security, always perform a full shutdown of your laptop before traveling. If your laptop remains on and is either lost or stolen while in transit, it presents a security concern. A complete shutdown of your pc minimizes the risk of unauthorized users accessing sensitive data through your computer.
Think Before You Click
Phishing remains a highly effective attack, exploiting the human factor by compelling recipients to click links or open suspicious attachments in emails. These emails often risk unintentionally providing credentials or installing malicious software, compromising both business and personal systems.
The Cybersecurity and Infrastructure Security Agency (CISA) advises: “If a link or attachment looks a little off, think before you click it – it may be an attempt to get sensitive information or install malware.”
Use Only Safe and Secure Wi-Fi
Industry Impact
Cybersecurity is important across all sectors, but it is important to understand how cyber threats affect YOUR world and industry. Below you will find resources and information regarding industry impact.

Public Sector
Addressing a breach in a public sector organization costs an average of $2.5 million. For a public school, that average typically rises to around $3.5 million. Whatever kind of public sector organization you lead, you have a duty to protect the personal information of those you serve and ensure your systems are consistently operational. To zero in on potential trouble spots in your organization's cybersecurity effort, review our Public Sector Cybersecurity Checklist and register for our Public Sector Cyber Webinar.
Cybersecurity Checklist
Manufacturing
The manufacturing sector is a prime target for cybersecurity attacks. On average, it takes 277 days to detect and contain a data breach. Given that manufacturing operations are directly tied to your revenue, prioritizing cybersecurity is crucial. In this discussion with Jessica Dore, we delve into how to build a robust IT security framework and ensure operational continuity for your manufacturing business.
Watch now
Healthcare
Healthcare providers encounter distinct cybersecurity challenges compared to other sectors. The typical expense to fix the damage caused by a cyberattack in healthcare practices is $9.77 million. That’s why it’s essential to fully understand what you can do to safeguard your practice and why your healthcare practice needs to prioritize cybersecurity and technology.
Read: How to Safeguard your practice
Construction
44% percent of construction companies have experienced project delays due to a cyberattack. In construction, any external factor — which includes cyberattacks — that delays your project can impact your bottom line. Check out our digital brochure to see how you can protect your construction business from cyber threats and ensure you continue building for the future.
Download the brochure
Financial Institutions
Due to the nature of their operations, financial institutions remain a prime target for cyber criminals, with the average cost for these institutions to repair the damage caused by a data breach being $6.08 million. This underscores the necessity for these organizations to prioritize cybersecurity. To learn more about protecting your organization, check out this Rehmann article.
Read Now
Dealerships
More than 15,000 car dealerships were affected by a recent cyberattack on cloud-based software provider CDK Global. Cyberattacks are on the rise across all industries, and car dealerships are no exception. To help you stay protected in uncertain times, we’ve developed a list of 10 practices to protect your dealership from present and future cyberattacks.
Get the listRecorded webinars

From the Office to the Shop Floor: Cybersecurity Training and Budgeting for Manufacturing
As the looming threat of cyberattacks grows at an alarming rate, it is important your public sector organization adapts to continue serving the best interest of your community. Watch the recording to learn how to maximize your resources and how to identify appropriate solutions to fill in any gaps in your technology infrastructure.

Maximizing Organizational Effectiveness Through Technology
As the looming threat of cyberattacks grows at an alarming rate, it is important your public sector organization adapts to continue serving the best interest of your community. Watch the recording to learn how to maximize your resources and how to identify appropriate solutions to fill in any gaps in your technology infrastructure.
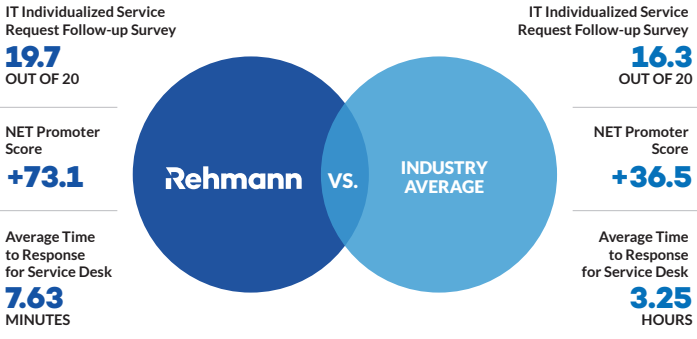
How Rehmann Compares
Our goal is to be there for your organization when you need help. In this fast-paced world, we know that IT problems and cyberattacks are a real threat to your organization’s success, which is why we take pride in being an industry leader in both managed IT services and tailored cybersecurity solutions.
To see how we stack up against the industry average, take a look at the verifiable stats below or click here to learn more.
Check out our digital brochure to learn more about Rehmann Technology Solutions and how we can elevate your organization’s IT.
Why Rehmann?
At Rehmann, we’re obsessed with client success. Because we know that no two organizations are alike, we take time to understand each organization we serve, tailoring customized solutions that achieve results that align with their short and long-term goals.
Take a moment to watch our video and listen to our valued clients and advisors as they share their experiences, unveiling why Rehmann sets itself apart from the rest.






